1.
Matlab/Octave Implementations
In this page, the Octave/Matlab implementations of eight lightweight
block ciphers are available:
|
Block
Cipher
|
Publication
year
|
Type of
construction
|
Block
size(s)
|
Key
size(s)
|
Files
|
|
HIGHT [1]
|
2006 |
Feistel network |
64 |
128 |
link |
|
Present [2]
|
2007 |
Substitution and permutation network |
64 |
80/128 |
link |
|
Ktantan [3]
|
2009 |
Stream/Block |
32/48/64 |
80 |
link |
|
LBlock [4]
|
2011 |
Feistel network |
64 |
80 |
link |
|
LED [5]
|
2011 |
Substitution and permutation network |
64 |
64/128 |
link |
|
Klein [6]
|
2012 |
Substitution and permutation network |
64 |
64/80/96 |
link |
|
ITUBee [7]
|
2013 |
Feistel network |
80 |
80 |
link |
|
Lilliput [8]
|
2015 |
Feistel network |
64 |
80 |
link |
These software implementations
help debugging hardware implementation because of the simplicity to
extract intermediate values. Additionally, it allows a designer to
generated new test vectors easily. For each block ciphers, two files
are provided: (Cipher)_lib.m and (Cipher).m (Example: LILLIPUT_lib.m
and LILLIPUT.m).
The first file contains the
library of all function used in the block
cipher implemented. The second file encrypts and decrypts messages
2. Hardware implementation
The hardware implementations of four of these block ciphers are also
available for FPGA:
| Block cipher
|
Used block size
|
Used key size
|
Fullwidth hardware implementation
|
Serial hardware implementation
|
| Klein
|
64
|
80
|
files
|
files
|
| Led
|
64
|
128
|
files
|
files
|
| Lilliput
|
64
|
80
|
files
|
files
|
| Ktantan
|
64
|
80
|
files
|
files
|
All these block ciphers have been implemented with two different
strategies: Full-width and Serial hardware implementations.
Additionally, the common framework built for the comparison of these
hardware implementations of block ciphers is also available to download
(files)
For Lilliput, four different
implementations are provided with four
different versions of the key schedule. In each archive, Lilliput_(i)
refers to version (i) of the key schedule. The Figure bellow presents
the four versions of the keyschedule.
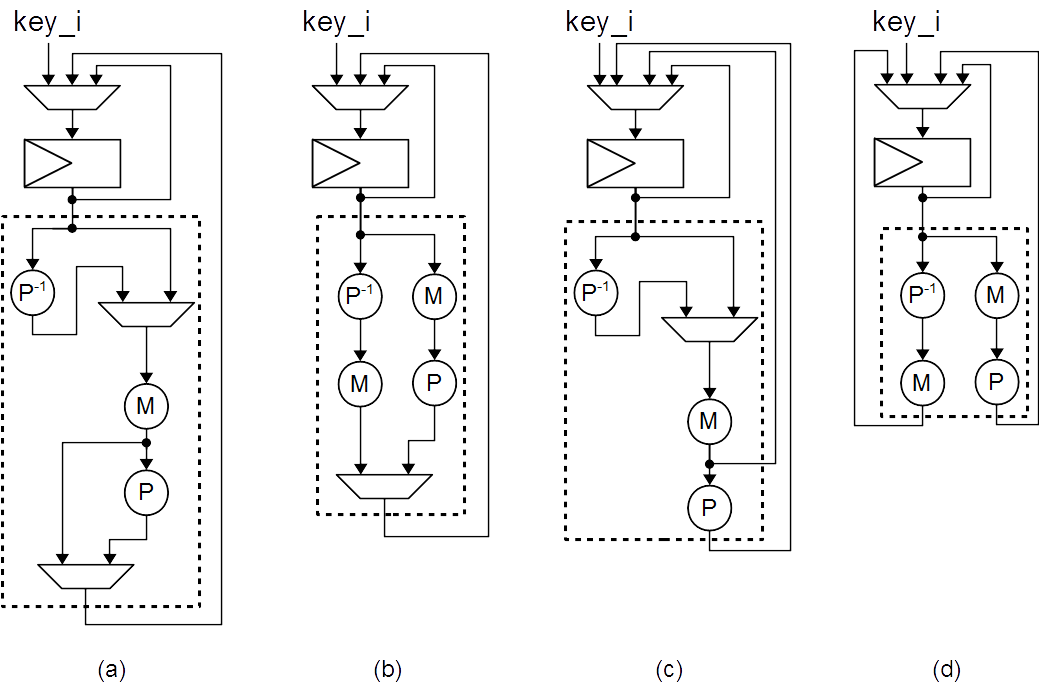
The specification of all implemented
ciphers can be found in the
reference list (Se
The specification of all implemented ciphers can be found in the
reference list (Section 4).
3. The common framework
The common framework divides the
implementation in two parts: the data
path and the controller. The Figure below presents the block diagram of
this framework.

The controller defines the interface of communication thanks to the
signal control:
|
Value of the signal control |
Command
sent to
the controller |
| 00 |
Do nothing |
| 01 |
Load a key |
| 10 |
Encrypt a
message |
| 11 |
Decrypt a
message |
The three outputs of the controller give information of the state of
the whole system:
| Output
signal |
Information
of the signal when it is set to 1 |
| key_valid |
A key is ready
to be processed: it is possible to encrypt or decrypt a message |
| busy_o |
The system is
performing an operation, all command will be ignore |
| done_o |
The operation
is done; the result is available at the data_o output. |
The Figure below shows the ASM chart of the controller.
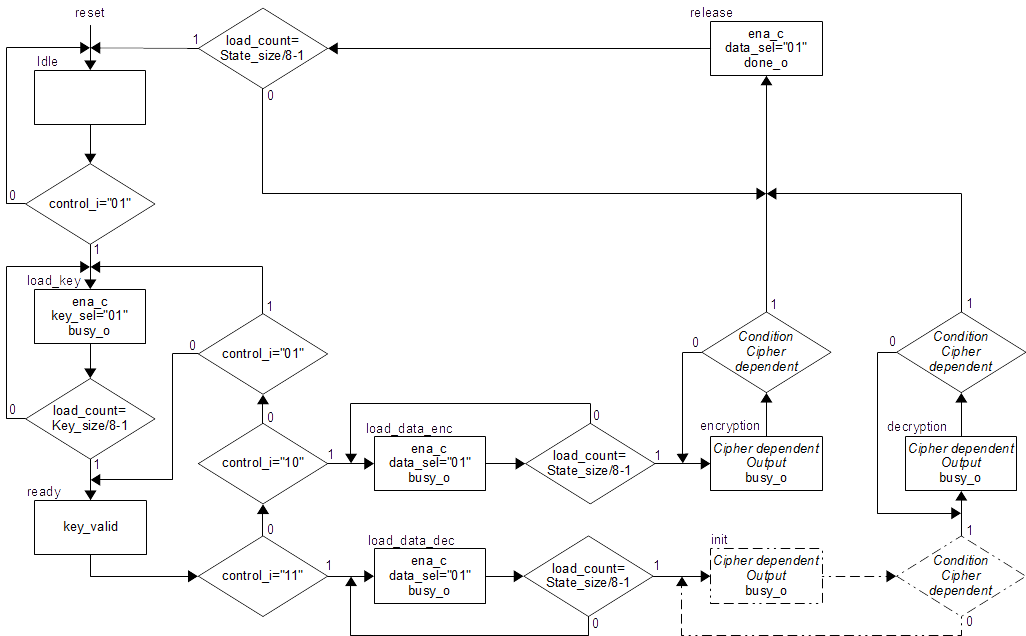
Only few part of this controller has to be changed depending on the
implemented algorithm. This feature makes possible to do fair
comparison of several block ciphers but also of other kind of
algorithms.
4. References
| 1. |
Hong D., Sung
J., Hong S., Lim J., Lee S., Koo B. S., ..., Kim H. “HIGHT: A new block
cipher suitable for low-resource device.” In Cryptographic Hardware and
Embedded Systems-CHES 2006, pp.46-59. DOI:
10.1007/11894063 |
| 2. |
Bogdanov A.,
Knudsen L. R., Leander G., Paar C., Poschmann A., Robshaw M. J., ...,
Vikkelsoe C. “PRESENT: An ultra-lightweight block cipher” Springer
Berlin Heidelberg, pp. 450-466. 2007,
DOI: 10.1007/978-3-540-74735-2_31 |
| 3. |
De Cannière C.,
Dunkelman O., Kneevi M., “Katan and ktantan a family of small and
efficient hardware-oriented block ciphers”. In Cryptographic Hardware
and Embedded Systems-CHES 2009, vol. 5747, pp. 272–288. DOI:
10.1007/978-3-642-04138-9_20 |
| 4. |
Wu W., Zhang L.
“LBlock: a lightweight block cipher”. In Applied Cryptography and
Network Security 2011, pp. 327-344. DOI:
10.1007/978-3-642-21554-4 |
| 5. |
Guo J., Peyrin
T., Poschmann A., Robshaw M., “The led block cipher”. In Cryptographic
Hardware and Embedded Systems-CHES vol. 6917, pp. 326–341. DOI:
10.1007/978-3-642-23951-9_22 |
| 6. |
Gong Z., Nikova
S., Law Y., “Klein: A new family of lightweight block ciphers”. In
RFID. Security and Privacy, Lecture Notes in Computer Science, vol.
7055, pp. 1–18. 2012. DOI:
10.1007/978-3-642-25286-0_1 |
| 7. |
Karakoç F.,
Demirci H., Harmancı A. E., “ITUbee: a software oriented lightweight
block cipher”. In Lightweight Cryptography for Security and Privacy
2013 pp. 16-27. DOI:
10.1007/978-3-642-40392-7 |
| 8. |
Berger T.,
Francq J., Minier M., Thomas G.: “Extended generalized Feistel neworks
using matrix representation to propose a new lightweight block cipher:
Lilliput”. IEEE Transactions on Computer (2015). DOI
10.1109/TC.2015.2468218 |



